Watch Zero-Touch Automation of Joiners, Movers & Leavers in a 10-Minute Mini Demo
See how Hire2Retire connects HR to Identity for Privilege & Access Management, ensuring a Superior First Day at Work with Role-Based Access Control, Security, Compliance & Governance.
Watch Zero-Touch Automation of Joiners, Movers & Leavers in a 10-Minute Mini Demo
Automate JML to Reduce HR & IT Workload by 70% & Cost by 60%
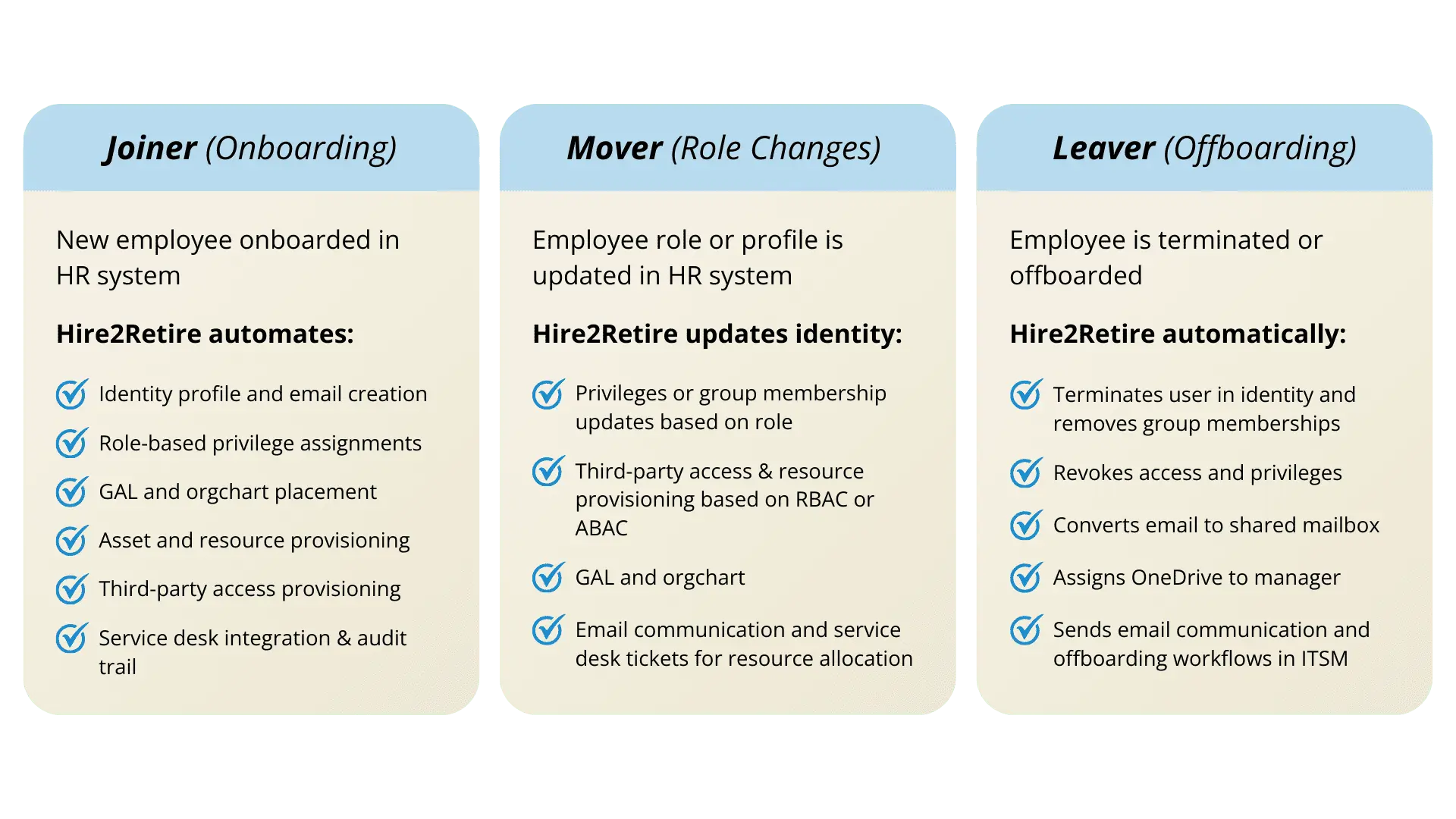
Automate Joiner, Mover, Leaver to Identity
Trusted by Leading Companies
These are some of the leading companies that have trusted RoboMQ to solve their HR system integration needs to accelerate digital transformation and create competitive advantages.
These are some of the leading companies that have trusted RoboMQ to solve their HR system integration needs to accelerate digital transformation and create competitive advantages.

Top-Rated IGA Solution For Ease of Use & ROI
Powerful Lightweight IGA platform with Data, ITSM & HR System Integration
Identity, Governance and Administration (IGA) with strong API and Data Integration capabilities from a leading iPaaS company at a fraction of the cost.



Choose your HCM platform to integrate with AD or Azure AD
RoboMQ is not affiliated, associated, authorized, endorsed by, or in any way officially connected with any of the HR systems. All product and company names are the registered trademarks of their original owners. The use of any trade name or trademark is for identification and reference purposes only and does not imply any association with the trademark holder of their product brand.
Choose your HCM platform to integrate with AD or Azure AD
RoboMQ is not affiliated, associated, authorized, endorsed by, or in any way officially connected with any of the HR systems. All product and company names are the registered trademarks of their original owners.
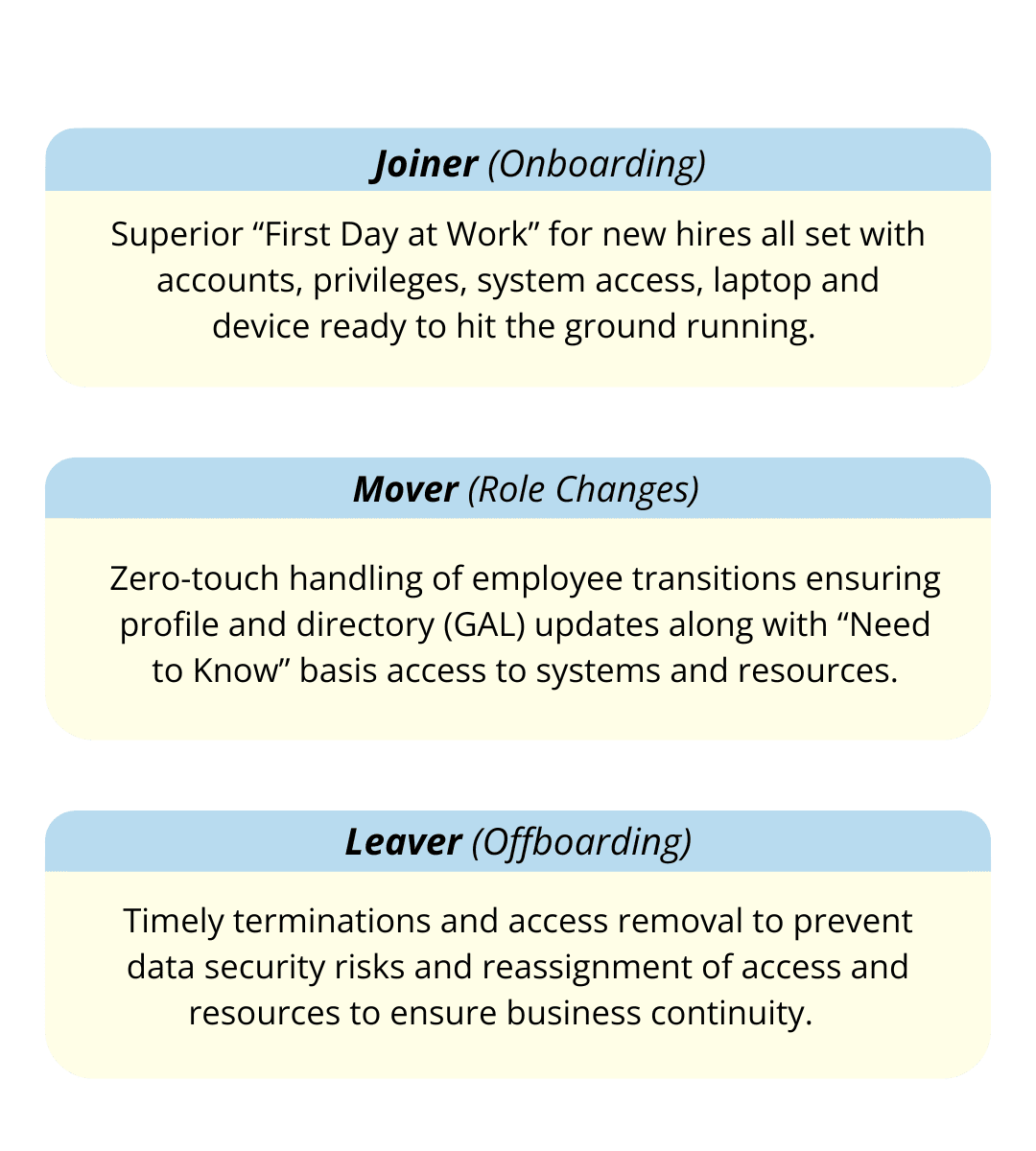
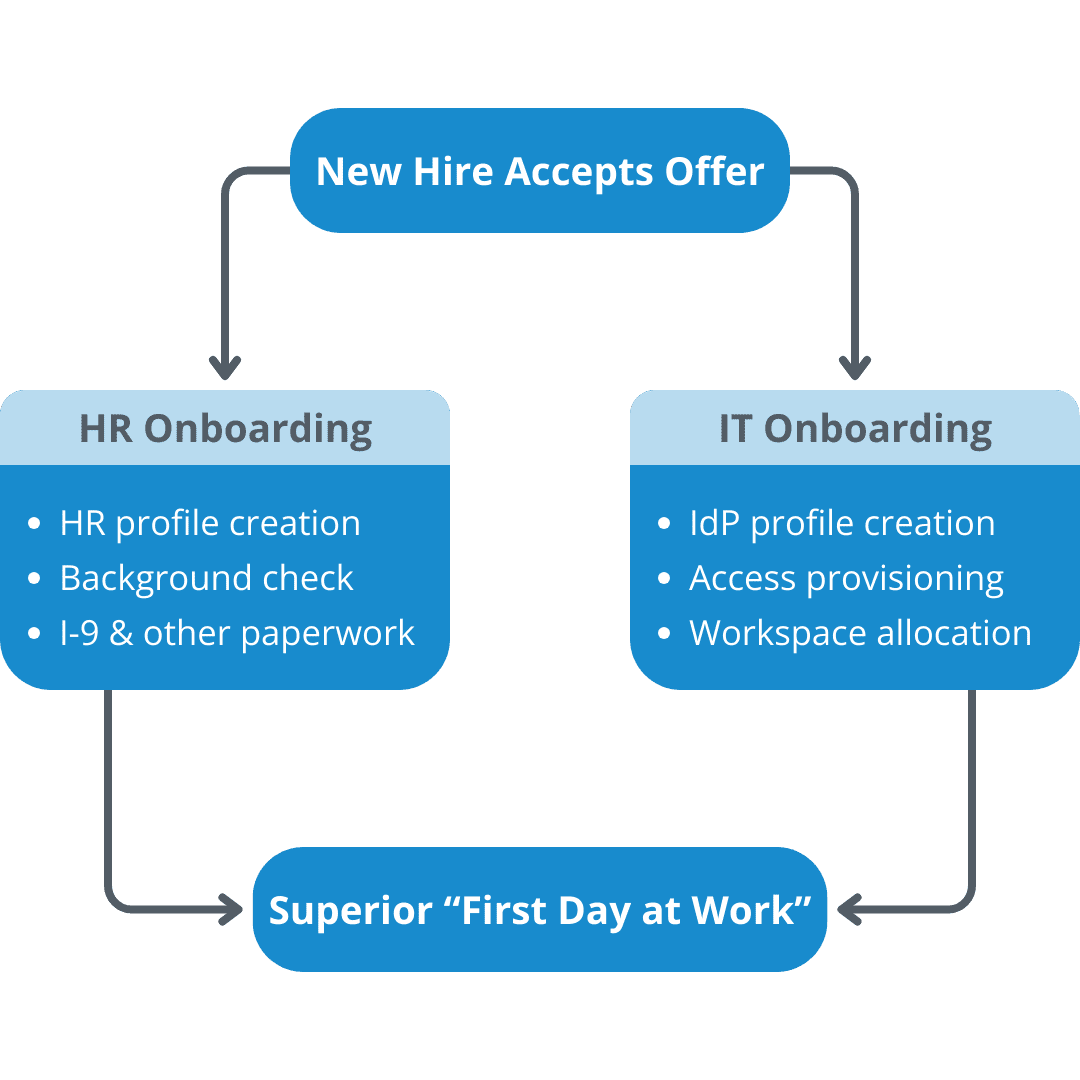
Automated Employee Onboarding for a Superior "First Day at Work"
Upon offer acceptance, while new hires are getting onboarded by HR, IT can, in parallel, get the account created and prepare and ship the laptop or devices so that the employee is ready for work on Day One!
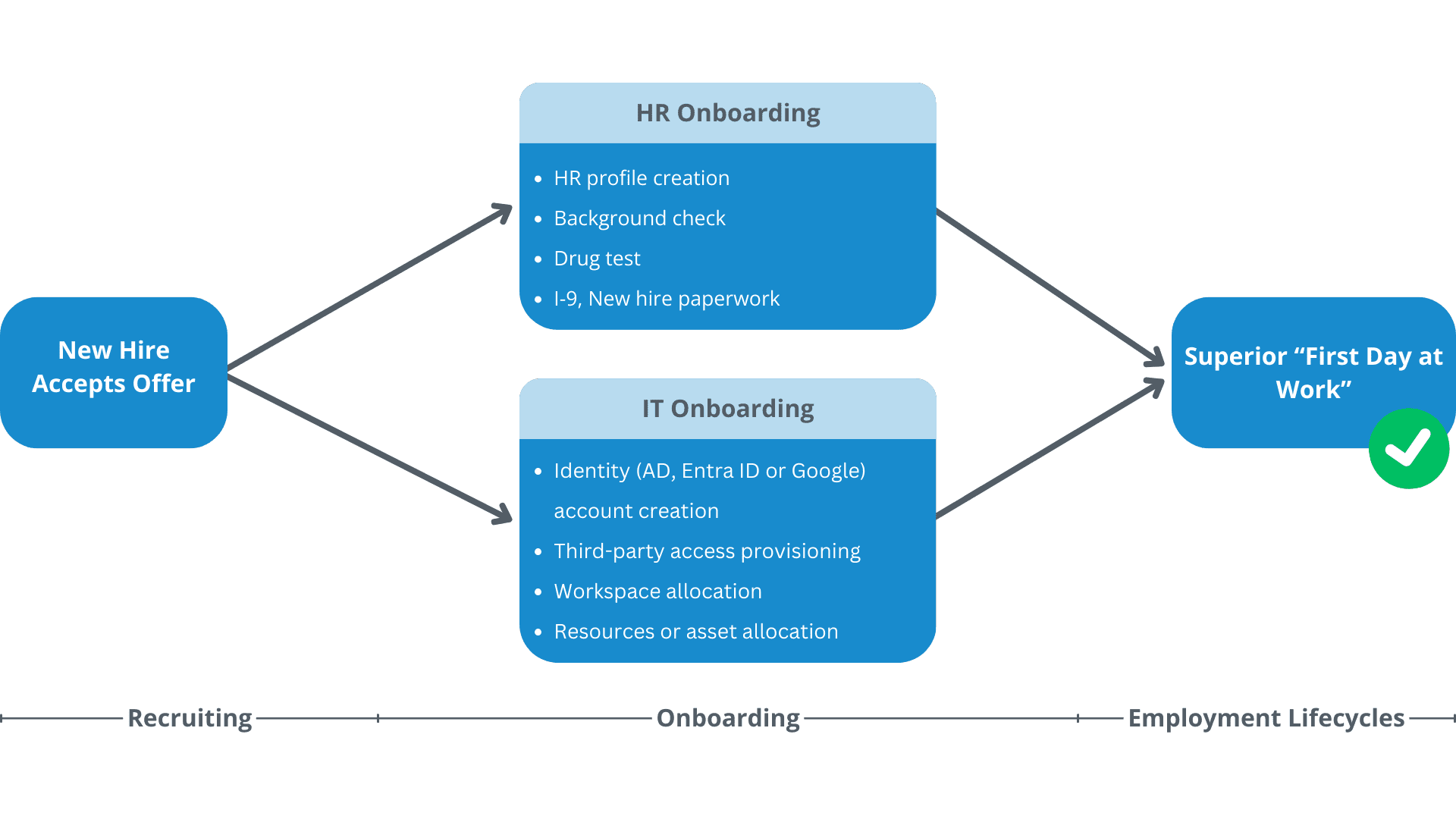
Automated Onboarding for a Superior "First Day at Work"
Why Hire2Retire for Employee Onboarding, Offboarding, and Transitions?
Leading companies use Hire2Retire to sync HR systems with Identity Providers (IdP) to manage workforce identity lifecycle and enable zero-touch privileges, access, and resource provisioning
Leading companies use Hire2Retire to sync HR systems with Identity Providers (IdP) to manage workforce identity lifecycle and enable zero-touch privileges, access, and resource provisioning

Superior “First Day at Work” experience
Superior “First Day at Work” experience

90% or more cost avoidance
90% or more cost avoidance

Role-based access and privileges
Role-based access and privileges

Timely terminations to prevent security risks
Timely terminations to prevent security risks

Security and Compliance with SOC2, HIPAA, ISO 27001
Security and Compliance with SOC2, HIPAA, ISO 27001
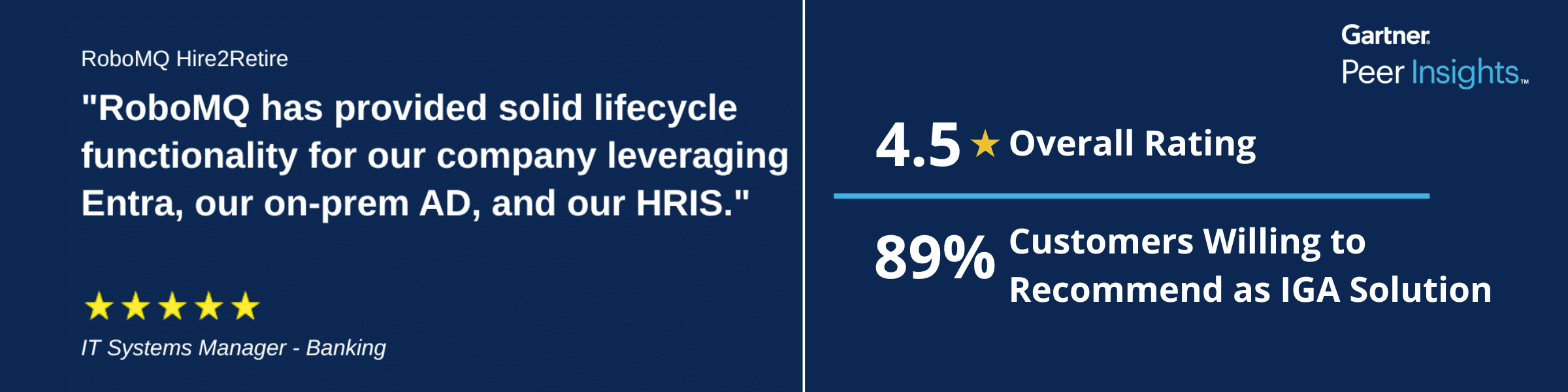
Hear from our Customers








Ready to see Workforce Identity Lifecycle Automation in Action?
Automate onboarding and offboarding with Hire2Retire integration. Manage profile changes from HR to Identity effortlessly while ensuring “need to know” basis access privileges to prevent cyber security and reputation risks.